7 LMS Security Features for a Safe Learning Environment

In today’s digital age, safeguarding sensitive data is a top priority for organizations using learning management systems (LMSs). Will confidential information remain protected? Who will have access to training materials? Addressing these and other concerns is important to maintain trust and security in any learning environment.
In this article, we will explore seven important LMS security features that protect against threats like viruses, spam, and hackers and provide peace of mind and safe learning experiences for all users. We’ll also highlight how the iSpring Learn LMS utilizes these security measures to enhance user confidence and protection.
Why Is LMS Security Important?
LMS security is crucial for several reasons:
- Protection of sensitive data: Imagine your employees’ personal details, grades, or learning progress falling into the wrong hands. LMS security features protect this sensitive data, ensuring that only authorized users have access.
- Compliance with regulations: With regulations like GDPR and FERPA, maintaining LMS security requirements isn’t just good practice; it’s a legal necessity. Secure learning management systems help organizations stay compliant and avoid hefty fines and/or legal troubles.
- Maintenance of trust: Trust is the foundation of any educational relationship. When learners and educators know their data is secure, it builds confidence that leads to more active participation and a positive learning environment.
- Prevention of disruptions: Security breaches can disrupt access to training courses. By prioritizing data security, organizations can ensure that learning continues smoothly without unexpected interruptions.
In a nutshell, LMS security isn’t just about preventing threats — it’s about creating a safe, reliable, and trustworthy environment where learning can thrive.
Key LMS Security Features to Consider
Here are seven key security features that will help keep your data safe and sound:
1. Password requirements
When it comes to keeping your LMS safe, having strong password rules is extremely important. After all, we want to make sure that only the appropriate people with the correct login credentials can access all the valuable educational content. Here are the elements of a strong password:
- Minimum length: Passwords with at least 8 characters are generally more secure. Longer passwords tend to be harder to crack.
- Complexity: Passwords should include a mix of uppercase and lowercase letters, numbers, and special characters. This variety makes it more challenging for unauthorized users to guess passwords.
- Avoiding common choices: Common passwords like “password123” or “12345678” are often the first targets for attackers. Many systems now block these from being used to enhance LMS data security and privacy.
iSpring Learn requires that every password be at least six characters long and should include at least one uppercase letter and one number. This helps protect against the use of simple passwords that can be easily cracked with dictionary attacks.
2. Data encryption
Data encryption is a security measure that ensures that personal information, such as usernames, passwords, and learning progress, remains protected as it travels between desktops or mobile devices, the LMS, and other apps or servers. This process turns your data into a secret code that only authorized individuals can unlock, protecting it from cyber threats.
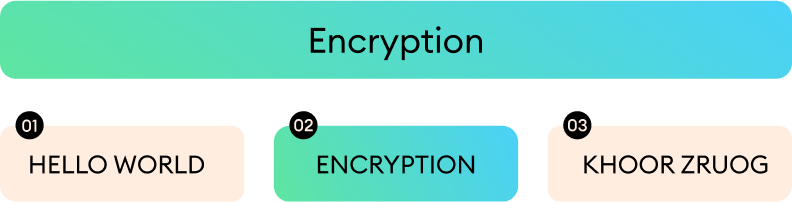
In iSpring Learn, encryption is used both when data is moving (in transit) and when it’s stored (at rest). For data in transit, iSpring Learn uses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) to create secure connections between users and the platform. This means that even if someone intercepts the data, they won’t be able to read it.
For data at rest, iSpring Learn encrypts stored information, adding an extra layer of protection. This is excellent news, especially for those who must comply with stringent regulatory standards, like healthcare and financial service organizations.
3. Data center physical security
Another critical step in safeguarding learning management systems is ensuring robust physical security for data centers. This means using facilities that are well-protected against unauthorized access and potential threats.
iSpring does a great job in this regard by collaborating with multiple hosting providers that meet high-level security standards. That way, if something goes wrong with one, a rapid switch to another keeps everything running smoothly.
iSpring uses several trusted providers:
- Liquid Web
- Amazon Web Services (AWS): ISO 27001 certified
- FirstColo: ISO 27001 certified
- Leaseweb: ISO 27001 certified
These providers make sure the data centers are secure by restricting physical access according to strict standards like SSAE 16 and ISO 27001.
4. Data backups and storage
Having a solid plan for storing and backing up data is key. While traditional backups are helpful, having a strong storage strategy can really amp up security and privacy.
Instead of just relying on regular backups, iSpring uses continuous data protection. This means data is constantly being saved in real time, which helps prevent any loss and keeps things running smoothly, even if there’s a hardware hiccup.
iSpring also makes sure that all data is stored in multiple physical locations. This isn’t just for files that customers upload; it also includes the data in their databases. All this helps reduce
the risk of losing content if something goes wrong. However, customers’ databases are backed up on a daily basis as well.
5. User roles
User roles in an LMS are like different hats people wear, each with its own set of responsibilities and permissions. These roles help keep the system organized and secure by ensuring that each person can only access what they need for their specific tasks.
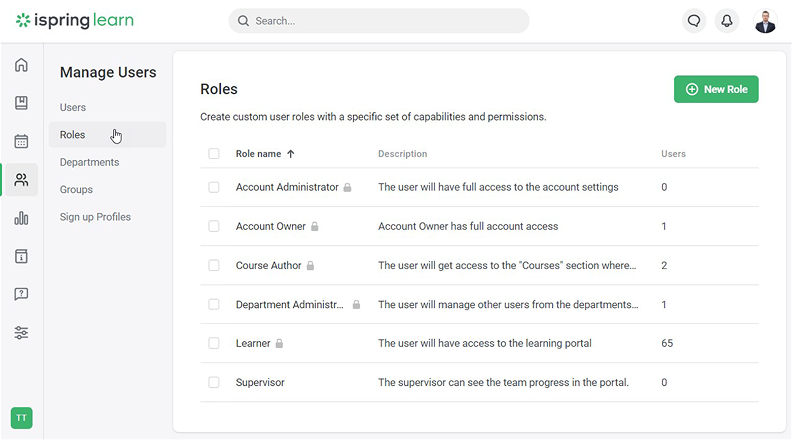
iSpring Learn utilizes the following standard user roles:
- Account Owner: Has the broadest permissions, including full account control and access to billing options. This role cannot be edited or deleted.
- Account Administrator: Helps the Account Owner with system and user management, having similar permissions but no access to billing.
- Department Administrator: Manages users in their department, limiting access to departmental data.
- Course Author: Creates and edits courses, with permissions restricted to content management.
- Learner: Has minimal permissions, primarily accessing courses and viewing activity history.
- Supervisor: Monitors learner progress and departmental statistics.
6. Logging and monitoring
Keeping an LMS secure also relies on smart logging and monitoring. These help track user activities and system events, like who logs in, what content is accessed, and any changes that are made. This process is crucial for identifying potential LMS security vulnerabilities.
Real-time monitoring tools alert administrators to unusual activities, such as repeated failed login attempts or access from unexpected locations. This allows for quick responses to potential threats and helps reduce the risk of damage.
iSpring uses an automated system to provide a high level of service performance and availability. This system conducts regular checks on services and sends alerts via email, instant messages, or SMS if anything unusual occurs. Besides, iSpring’s technical support team is available 24/7 and is always prepared to address any issues promptly.
7. Compliance with standards and regulations
For LMS providers, compliance often involves following various industry standards and legal requirements, such as GDPR for data protection in Europe, FERPA for educational records in the United States, and other relevant regional regulations. These standards dictate how personal data should be collected, stored, and processed.
iSpring Learn takes compliance seriously by implementing robust security measures that align with these standards. The platform is designed to protect user data through encryption, secure access controls, and regular security audits. Moreover, iSpring Learn offers tools like customizable privacy settings and detailed access logs to help organizations meet their compliance needs.
On-Premise LMS for Enhanced Security
For organizations with stringent security requirements, iSpring offers the option to deploy an on-premise LMS. This solution allows you to integrate the learning platform into your private IT infrastructure so that all corporate data remains in-house. By doing so, you maintain complete control over data storage and access and can fully align with your internal security policies and industry standards.
The on-premise LMS from iSpring Learn provides all the features of its cloud-based counterpart, including interactive courses, detailed analytics, and user-friendly interfaces, while allowing for a custom installation tailored to your specific needs.
Conclusion
When choosing an LMS, prioritizing strong security features is important. Look for systems that include comprehensive activity tracking, reliable data backups, secure storage, stringent password requirements, and data encryption. This ensures that your data stays protected and builds trust in the platform. It’s also important to check that the LMS complies with regulations like GDPR to safeguard your information. If you need an especially secure learning platform, opt for an on-premise LMS.
If you’re considering an LMS with top-notch security features, why not try iSpring Learn? It’s designed to keep your data safe while providing a user-friendly learning experience. Book a free LMS demo and see how iSpring Learn can enhance your training process.







